Cybersecurity Exposure Management: A Practical Guide
In today’s interconnected world, organizations face a relentless barrage of cyber threats. Cybersecurity exposure management is a proactive and continuous approach designed to help organizations understand, reduce, and manage their cybersecurity risks effectively. It’s about looking at your digital environment through the eyes of an attacker to identify and mitigate weaknesses before they can be exploited.
What is Cybersecurity Exposure Management?
Cybersecurity exposure management is a comprehensive process that goes beyond traditional vulnerability scanning. It involves continuously identifying, analyzing, prioritizing, and remediating all potential weaknesses and misconfigurations across an organization’s entire digital footprint. This holistic view includes everything from networks and applications to cloud environments and connected devices.
Primary Goals of Exposure Management
The primary goal of cybersecurity exposure management is to identify, prioritize, and manage cybersecurity risks to reduce the organization’s attack surface. This involves:
- Proactive Identification: Continuously discovering vulnerabilities and misconfigurations.
- Risk-Based Prioritization: Assessing the actual risk posed by exposures in the context of business impact.
- Effective Remediation: Taking timely action to fix or mitigate identified weaknesses.
- Continuous Improvement: Ensuring that security posture improves over time in response to evolving threats.
Core Concepts in Cybersecurity
Understanding fundamental cybersecurity terminology is crucial for grasping exposure management.
Vulnerability
A vulnerability is a defect in software code that can be used to gain unauthorized access to a system. More broadly, it’s any weakness or flaw in a system, application, or network that could be exploited by a threat actor to compromise the confidentiality, integrity, or availability of data or systems. These can arise from coding errors, misconfigurations, design flaws, or even human error.
Threat Model
The purpose of a threat model in cybersecurity exposure management is to identify potential attack vectors and prioritize defenses. Threat modeling is a structured process that helps an organization understand what parts of its systems are most vulnerable to attack, who might attack them, and how. By thinking like an attacker, organizations can proactively identify potential attack paths and implement appropriate security controls.
Attack Surface
The attack surface in cybersecurity is the area of an organization’s network or system that is vulnerable to cyber attacks. It represents the sum of all the different points or “attack vectors” where an unauthorized user can try to enter data to or extract data from an environment, and where an attacker can attempt to compromise a system.
Example of an attack surface in a typical corporate network: The range of devices and applications that can be accessed by an employee’s login credentials. Every endpoint (laptops, mobile devices), every application (web apps, SaaS, on-premise software), and every network service accessible represents a potential entry point if not properly secured.
Attack Path
An attack path in cybersecurity is the sequence of steps taken by a hacker to carry out a cyber attack. It’s a chain of interconnected vulnerabilities and misconfigurations that an attacker can exploit, moving laterally or escalating privileges, to achieve a specific objective, such as gaining access to sensitive data or disrupting operations.
Purpose of mapping attack paths: The primary purpose of mapping attack paths is to identify vulnerabilities in a system that can be exploited by a cyber attack. By visualizing these paths, organizations can pinpoint critical weaknesses and break the chain of exploitation before an attacker can succeed.
Zero-Day Vulnerability
A zero-day vulnerability is a security flaw that is known to attackers but not yet known to the software vendor or security community. This means that the vendor has had “zero days” to fix the flaw before it’s actively exploited in the wild, making these vulnerabilities particularly dangerous.
Privileged Access
Cybersecurity privileged access refers to access to administrative systems and tools granted to IT personnel. It involves special, elevated permissions that allow users (or processes) to perform critical system functions, manage configurations, install software, or access highly sensitive data across an organization’s IT infrastructure. This type of access is powerful and, if compromised, can lead to severe breaches.
Credential Caching
Cybersecurity credential caching is a process of storing login credentials on a user’s device for easy access. While convenient for users, cached credentials can become a significant security risk if not properly protected, as an attacker gaining access to the device could potentially retrieve these stored credentials.
Software Patches and Updates
A common cause of cybersecurity vulnerabilities in software applications is failing to apply software patches and updates. Software vendors regularly release patches and updates to fix known security flaws. When these are not applied in a timely manner, systems remain vulnerable to exploits that target these known weaknesses.
Key Processes and Frameworks
Several processes and frameworks underpin effective cybersecurity exposure management.
Vulnerability Assessment
A vulnerability assessment is a proactive process to identify and prioritize weaknesses in systems and networks. Its primary goal is to identify and prioritize vulnerabilities for remediation. It involves scanning and analyzing systems for known security flaws.
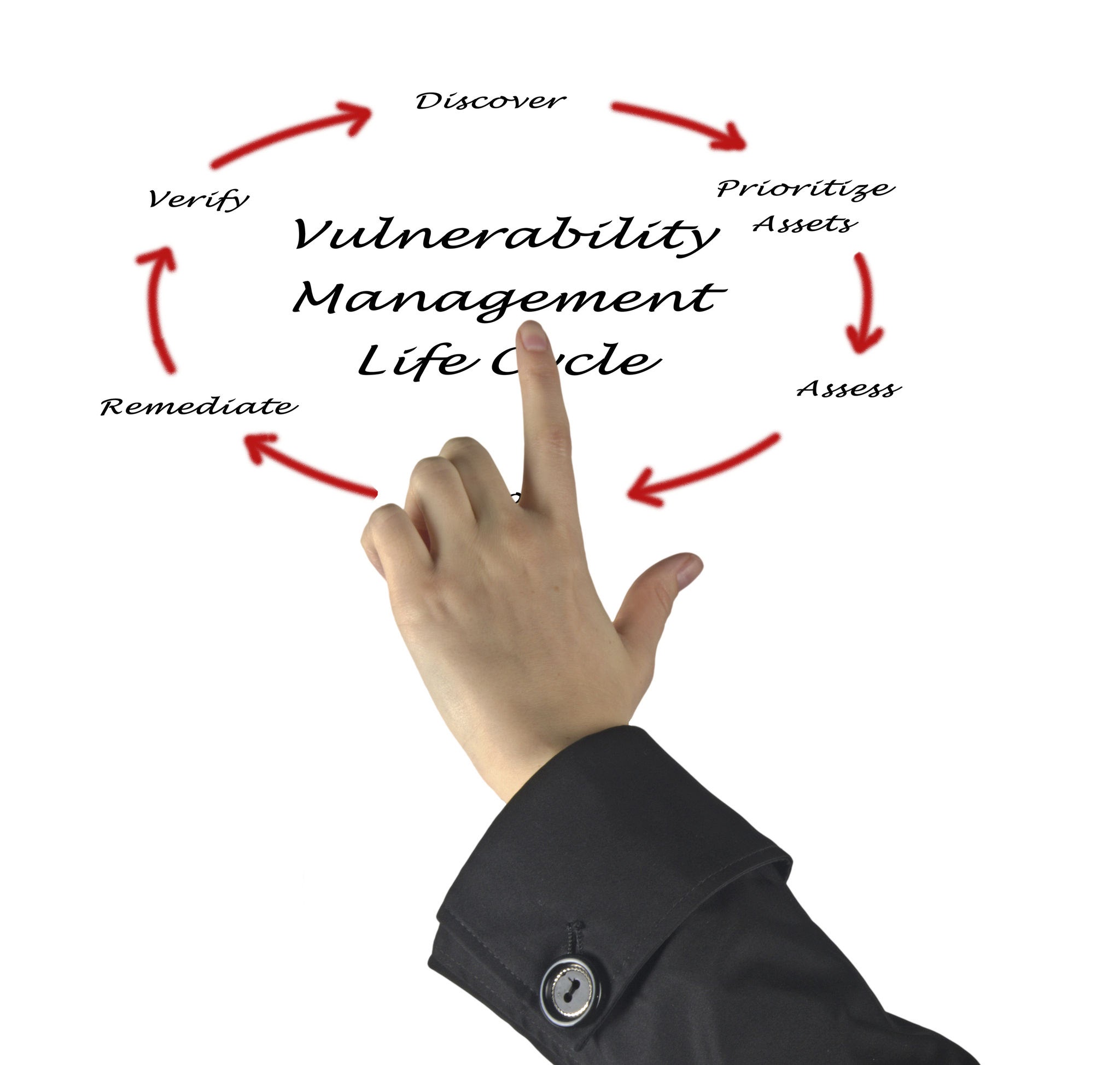
Vulnerability Management
Vulnerability management is a comprehensive process that helps organizations manage and track the status of remediation efforts for identified vulnerabilities. It’s a continuous cycle that includes identifying, assessing, prioritizing, treating (remediating), and reporting on security vulnerabilities.
Security Control Frameworks (e.g., NIST CSF)
The purpose of a security control framework, like the NIST Cybersecurity Framework, in cybersecurity exposure management is to provide a structured approach for implementing and managing security controls. These frameworks offer guidelines, best practices, and a common language to help organizations establish and improve their cybersecurity posture consistently. They act as a blueprint for building a robust security program.
Cybersecurity Control Validation
Cybersecurity control validation is the process of testing the effectiveness of cybersecurity controls. It ensures that the security measures an organization has implemented are actually working as intended against real-world threats.
Common method for validating cybersecurity controls: Conducting a penetration test is a common and highly effective method. A penetration test simulates a real cyber attack to evaluate the effectiveness of an organization’s security controls and identify exploitable vulnerabilities.
Continuous Monitoring
The goal of continuous monitoring in cybersecurity control validation is to detect and respond to cyber threats in real-time. Continuous monitoring provides ongoing visibility into the security state of systems and networks, allowing organizations to quickly identify and react to suspicious activities or control failures.
Risk Management
Risk management is the process used to prioritize the remediation of identified vulnerabilities based on the risk they pose to an organization. It involves identifying, assessing, and controlling risks by considering both the likelihood of a threat exploiting a vulnerability and the potential impact of such an event. It helps organizations make informed decisions about where to invest their security resources.
Risk management is also a process used to identify potential sources of cyber threats and vulnerabilities in an organization’s IT systems and networks. By encompassing both threat identification and vulnerability discovery, it provides a holistic view of potential dangers.
Incident Response
Incident response is a structured approach for dealing with security incidents, typically after a breach has occurred. While crucial for minimizing damage, it is a reactive process, distinct from the proactive identification and prioritization done in vulnerability management or risk assessment.
Roles and Responsibilities
Effective cybersecurity exposure management relies on dedicated roles within an organization.
Chief Information Security Officer (CISO)
The Chief Information Security Officer (CISO) is a senior executive whose role is to oversee the organization’s information security program and ensure it aligns with business goals. The CISO is ultimately accountable for the organization’s cybersecurity posture.
The primary concern of a CISO is protecting the organization’s digital assets from cyber threats. This overarching responsibility guides all their strategic and operational decisions regarding security.
Purpose of a CISO reporting to a board of directors on cybersecurity matters: The purpose is to ensure that the board understands the organization’s cybersecurity risks and the measures being taken to mitigate them. This enables the board to fulfill its governance responsibilities, make informed decisions about risk acceptance, and allocate necessary resources for security.
Cybersecurity GRC Analyst
The role of a cybersecurity GRC (Governance, Risk, and Compliance) analyst is best described as monitoring and assessing an organization’s cybersecurity risks and compliance. They ensure that the organization adheres to relevant laws, regulations, industry standards, and internal policies, and that security practices are aligned with overall business governance.
Metrics in Cybersecurity Exposure Management
Metrics are essential for understanding, communicating, and improving an organization’s security posture.
The Value of Metrics
A key value to exposure management from a metrics perspective is that it ensures silo’d metrics are rolled up to provide a cyber risk picture for leaders. Instead of disparate reports from individual security tools, exposure management aggregates data into a cohesive, actionable view of overall risk, enabling better strategic decisions.
Key Metrics for Measuring Exposure
A useful cybersecurity metric for an organization is the average time taken to detect and respond to a security incident. This metric (often referred to as Mean Time To Detect – MTTD, and Mean Time To Respond – MTTR) directly indicates the efficiency and effectiveness of security operations and incident response capabilities, reflecting how quickly an organization can identify and neutralize threats. Shorter times generally mean less impact from an incident.
Share this content: